
Wherever you are in this world, there is no escaping from the fact that the crypto age is before us, so much so that the International Monetary Fund (IMF) has coined the term “cryptoization”. The next time you engage in crypto talk, you can act like a know-it-all by sharing your knowledge about the genesis of cryptocurrency, which can be traced to October 2008. At that time, the pseudonymous Satoshi Nakamoto published Bitcoin (BTC)’s whitepaper on the cryptography mailing list of metzdowd.com.
Since then, crypto has grown into a multi-trillion dollar market with an all-time high capitalization of about USD2.9 trillion, which was recorded in November 2021. As for the trading volume of the crypto market, the all-time high peak was set on 20 May 2021, which recorded a 24-hour trading volume of about USD516 billion.
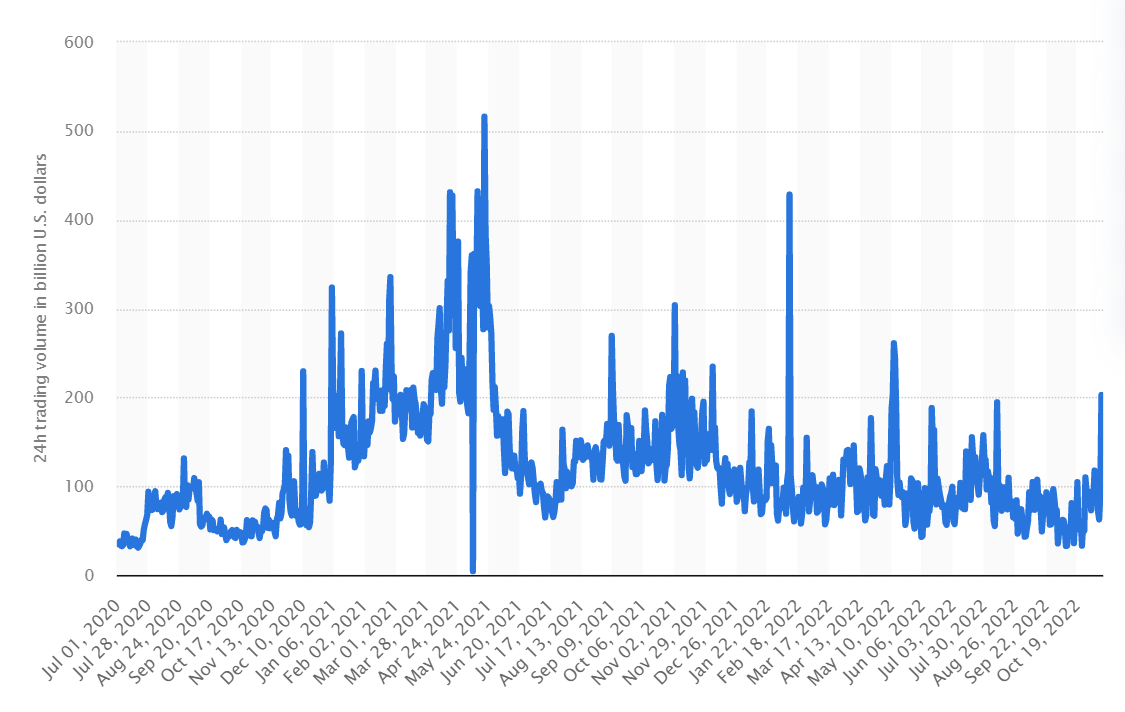 Trading Volume of the Crypto Market from July 2020 to Oct 2022 (Source: Statista.com)
Trading Volume of the Crypto Market from July 2020 to Oct 2022 (Source: Statista.com)
With all the fear, uncertainty, and doubt (FUD) thrown around, it's hard to keep track of the cyclical trends of the crypto market. In general, the crypto market is subject to 4-year cycles of upswings and downturns due to the coupling effects between the market and BTC, whose halving event occurs every four years. Throughout its bull and bear cycles, the crypto market has, more often than not, emerged more robust, which stands as a testament to its long-term viability. Instead of listening to the prophecies of the naysayers that the end is nigh for crypto, your time may be better spent learning a thing or two about the fundamentals of cryptocurrencies.
(a) Coins vs. TokensCryptocurrencies can be divided into coins and tokens. The key difference between coins and tokens is that coins have their native blockchain, whereas tokens operate using those of others. Examples of coins are BTC, Ether (ETH), and Binance Coin (BNB), which operate on the Bitcoin, Ethereum, and Binance blockchains, respectively. Examples of tokens are Ripple (XRP), a payment settlement token. Dai (DAI), which, although referred to as a stablecoin, is technically a token, and Axie Infinity Shards (AXS), the governance token for the Axie Infinity game.
 Coins vs. Tokens (Source: Avocado DAO)
Coins vs. Tokens (Source: Avocado DAO)
The taxonomy classification of coins is such that all coins other than BTC have been categorized as alternative coins (altcoins). Most coins function as units of account, but only a select few coins function as stores of value. Regarding their unit of account functions, most cryptocurrencies are generally divisible by eight or more decimal places. For example, the smallest unit of ETH (gwei), is divisible by nine decimal places, rendering it one billionth of an ETH.
Concerning their medium of exchange functions, coins can be used for the payment of gas fees for transactions carried out on the coin’s native blockchain or on decentralized applications (dapps) that are built on top of the blockchain. For example, BNB can be used to pay transaction fees on Binance’s exchange and dapps, which operates using Binance’s blockchains.
As for their store of value functions, this hinges on the ability of a coin to function as a hedge against inflation. In simple terms, the measurement of an inflationary hedge is based on the ability of a financial instrument to retain its value in the long term, as in whether there is substantial dilution in the instrument's value over a long time. In this regard, BTC is generally regarded as the gold standard for the store of value functions of coins. This has prompted some countries particularly those in Latin America to be exploring the possible pegging of their respective national currency to BTC. Leading the way is El Salvador which had in September 2021 adopted BTC as its national currency. However in recent times, ETH has emerged as an altcoin that serves as an alternative crypto store of value to BTC.
 Functions of Coins (Source: Avocado DAO)
Functions of Coins (Source: Avocado DAO)
Tokens can be categorized into governance, utility, payment, security, and stablecoins which, for reasons unknown, are not referred to as stabletokens.
(i) Governance Tokens
Governance tokens are cryptocurrencies that entitle their holders to put forth and vote on proposals concerning the management and operations of the issuer’s ecosystem. An example of a governance token is Uniswap (Uni) which entitles its holders to put forth and vote on proposals concerning the protocol's operations.
(ii) Utility Tokens
Utility tokens such as Filecoin (FIL) and Chainlink (LINK) can be used as a medium of exchange within the ecosystem of their issuer. Another notable example of a utility token is the Basic Attention Token (BAT), which can be used to purchase premium content and services within the Brave browser ecosystem. Users of Brave browsers who view privacy-respecting ads would earn BAT tokens whereas content creators could receive tips and donations in the form of BAT tokens. Payment tokens on the other hand can be used as a medium of exchange beyond the ecosystem of their issuer. Some examples of payment tokens are Bitcoin Cash (BCH), Dash (DASH) and Litecoin (LTC).
(iii) Security Tokens
Security tokens are cryptocurrencies that meet the definition of securities as set out in the Howey Test as laid down in the landmark case of SEC v. W. J. Howey Co. In essence, the Howey Test provides that a financial instrument would amount to a security if it is an investment contract. An investment contract involves an investment of money under a joint enterprise with the expectation of profits that are to be derived from the efforts of others.
Any token which falls within the scope of the investment contract would amount to a security and be prescribed as such according to the Howey Test. An example of a security token is the Blockchain Capital (BCAP) token which grants its holders rights to the network’s portfolio of funds.
(iv) Stablecoins
Stablecoins are tokens whose value is pegged to the underlying assets in their reserve basket. These underlying assets can be fiat, commodity, or other financial instruments such as bank deposits, treasury bonds, or even crypto assets. An example of a stablecoin is Tether (USDT), whose value is pegged to the United States Dollar (USD) on a 1:1 ratio. In general, there are four types of stablecoins namely fiat-backed, crypto-backed, commodity-backed, and algorithmic stablecoins.
Of the four types, algorithmic stablecoins are arguably the most risky store of value because unlike its peers, algorithimic stablecoins are not backed by any physical or digital assets. Instead the value of algorithmic stablecoins is maintained using algorithm mechanisms which could prove to be inadequate in times of high market volatility. Case in point is the crash of the algorithmic stablecoin Terra USD (UST) in May 2022 that wiped out USD45 billion from the crypto market.
 Types of Tokens (Source: Avocado DAO)
Types of Tokens (Source: Avocado DAO)
The plethora of cryptocurrencies with their distinctive uses and functions has allowed these currencies to integrate with multiple aspects of the economics and financial domains. This integration has played a crucial role in the dawn of the age of cryptoization.
(3) Technical Overview of CryptocurrenciesAs with any commodity, cryptocurrency, too, has its version of gold and silver. BTC is commonly referred to as digital gold, whereas ETH has been referred to as digital silver. The digital nature of cryptocurrencies means that garnering a functional understanding of these currencies would necessitate some discussions about their technical aspects. This includes their trading and storage options, consensus mechanisms as well as interoperability features.
 Technical Aspects of Blockchain and Crypto (Source: Avocado DAO)
Technical Aspects of Blockchain and Crypto (Source: Avocado DAO)
Trading of cryptocurrencies can be done through either a centralized exchange (CEX) or a decentralized exchange (DEX). A CEX operates using an order book through which the exchange matches orders from market makers (sellers) and market takers (buyers). A DEX, on the other hand, uses an automated market maker (AMM), which can be understood as a “money robot” whose algorithms are programmed to price assets automatically based on the mathematical formulae coded into their algorithms.
The use of AMM allows users to swap tokens through a liquidity pool that optimizes their deposits' contribution to the liquidity levels of the pool. Both CEXs and DEXs have their respective pros and cons, which is why the best tokens can be traded on both types of exchanges. An example of such a token is Avocado DAO (AVG) which powers the decentralized autonomous organization (DAO) of Avocado Guild. AVG tokens can be traded on CEXs such as MEXC as well as DEXs such as Uniswap.
The peer-to-peer (P2P) feature of DEX arises from the fact that other users provide liquidity in their pools. Although CEXs are simpler to use, DEXs offer better security due to the non-custodial nature of their operations. Similarly, non-custodial wallets for which the users themselves store private keys are generally safer than custodial wallets. In the crypto domain, there is a saying, “not your keys, not your coins”.
(b) Consensus MechanismsThe decentralized feature of blockchain means that there is no single party running the show which is why there’s a need for consensus mechanisms to facilitate collective decision-making. Consensus mechanisms refer to protocols that are used by a blockchain network to enable the achievement of agreement across the participating nodes which refer to devices of stakeholders on the network. The two main types of consensus mechanisms are Proof-of-Work (PoW) which is used by the Bitcoin network, and Proof-of-Stake (PoS), which is used by the Ethereum network.
(i) Proof-of-Work (PoW)
PoW requires the contribution of computing power to solve mathematical equations to deter malicious nodes from taking over the network. The reasoning is that if a malicious node intends to take over a network by controlling 51% or more of the network, this would require an astronomical amount of computing power which though implausible, is not impossible. In return for the nodes’ contributions towards securing a PoW network, the reward for participating nodes is the right to mine for the native cryptocurrency of the network, with a prime example being BTC mining.
Nodes are computers or other devices that are connected to a blockchain network and help validate transactions on the network. A malicious node is a node that is intentionally trying to disrupt or manipulate the normal functions of the blockchain network on which the node resides.
(ii) Proof-of-Stake (PoS)
PoS requires the locking up of cryptocurrencies in return for a right to validate transactions on the network. The reward for PoS is the receipt of interest in the form of the native cryptocurrency of the network upon the completion of the lock-up period. In September 2022, the Ethereum network, through an update codenamed The Merge migrated from PoW to PoS. This transition resulted in the Ethereum network being a green blockchain as it reduced the network's energy consumption by about 99.95%.
(c) Blockchain and Crypto InteroperabilityGiven the various blockchain networks comprising the crypto ecosystem, the interoperability of these networks through the use of cross-chain bridges and wrapped token is critical to the generation of network effects for the ecosystem.
(i) Cross-Chain Bridges
The advent of cross-chain bridges such as Binance Bridge has paved the way for the interoperability of blockchain networks. In simple terms, cross-chain bridges help transfer information and assets between different blockchain networks, thereby allowing for cross-chain transactions, which refer to transactions across different blockchain networks.
(ii) Wrapped Tokens
In tandem with the use of cross-chain bridges is the use of wrapped tokens such as Wrapped BTC (WBTC). In simple terms, wrapped tokens are converted cryptocurrencies that can be used on other blockchains besides their native blockchain. How it works is that the wrapped token would be pegged to the value of the cryptocurrency it represents before being transferred to another blockchain network. Once this transfer has been completed, the wrapped token is then unwrapped, after which it reverts to its original form.
The combination of cross-chain bridges and wrapped tokens has paved the way for the interoperability of cryptocurrencies across blockchain networks. This element of interoperability has allowed the ecosystem as a whole to benefit from the efficiencies arising from economies of scale and scope.
The application of blockchain technology is set to become increasingly sophisticated as the crypto market grows in maturity. In this context, Learn-and-Earn (L&E) courses under the banner of educational finance (EduFi) banner would play a key role in supporting blockchain and crypto education among the masses. A case in point is Avocado DAO’s Questing Portal which offers short Learn-and-Earn (L&E) courses on Web3-related topics with AVG tokens and non-fungible token (NFT) badges as completion rewards.
(4) ConclusionA decade and a half after the introduction of BTC, the crypto market has defied all odds to take on a life of its own. While the pseudonymous Satoshi Nakamoto remains mysteriously unidentified, one can safely assume that he/she/they would be pretty amazed by the age of cryptoization that his/her/their BTC pet project has catalyzed.
Test what you've learnt from this article at our Questing Portal.
In our next course, Why We Need to Connect to Web3, we would be exploring the next generation of the Internet, Web3.
The information in this article is neither intended as nor amounts to financial, tax, legal, investment, trading, or any other form of professional advice. Avocado DAO makes no representation whatsoever that the information herein is accurate, up to date, or applicable to the circumstances of any particular reader or organization.
The use of the information herein is entirely at the reader's own risk, who shall assume full responsibility for the risk of any loss or damages arising from their reliance on such information. For the avoidance of doubt, under no circumstances is Avocado DAO to be deemed as having assumed responsibility or be held liable for any loss or damages, whether financial or otherwise, arising from the reader's use of or reliance on the information herein.